ABB Ability™ Secure Remote Access (Use Case)
Secure by Design Remote Access solution for remote maintenance of industrial systems
As an independent component of ABB Ability™ History, ABB Ability™ Secure Remote Access (ABB Ability™ SRA) allows end-to-end secure access to resources over multiple network layers. ABB Ability™ SRA provides encrypted communications, authentication, authorisation, access control, and auditing to handle remote service activities to OT devices and systems effectively with minimum overhead. It only requires outbound HTTPS (443) connectivity from the more secure zone to the next network zone, with no need to open firewalls or proxy settings.
Industrial Cybersecurity Landscape
The aspiration for secure digital transformation remains relentless in the ever-evolving landscape of manufacturing and industrial operations.
Digital Transformation
Due to digital transformation and OT/IT convergence, ubiquitous cyber threats have expanded to the previously isolated operational technology (OT) environment. Although these newer types of connected devices underpin manufacturing, power generation, and other industrial processes, enabling safe, real-time data exchange to enhance efficiency and effectiveness, they also create opportunities for attackers to access these inherently insecure OT environments. A breach in one system can have cascading effects on others, amplifying the impact of cyber incidents.
Legacy Systems
Many industrial systems rely on outdated devices and technology that were not originally designed with cybersecurity or ongoing support in mind, making them challenging to secure. As digital transformation progresses, vulnerabilities in operational technology (OT) and industrial control systems (ICS) become more exploitable. Consequently, industrial organisations are encouraged to protect these systems and conduct thorough security assessments. However, modernising legacy systems to meet sustainability goals is becoming increasingly complex. Effectively securing outdated OT and ICS demands a strategic, multi-layered approach.
Remote Access
Remote access is considered a critical capability of modern industry. It allows engineers, technicians, and operators to monitor, diagnose, and manage OT and industrial control systems (ICS) without physical presence. Organisations rely on internal and third-party personnel to maintain assets, interact with these smart networked systems, and exchange real-time data to support and guarantee performance in safety-critical applications. This capability helps businesses optimise operations and reduce equipment monitoring, upgrades, and maintenance costs.
At the same time, increased connectivity introduces greater cybersecurity risks, threatening operational continuity, safety, and profitability. When granting access to third-party vendors and contractors into the organisation's OT environment, it poses a substantial risk if their access and connectivity privileges are not properly controlled. The unprecedented challenges of the OT environment make ordinary IT cyber solutions, such as Virtual Private Networks (VPNs), inadequate. As a result, robust security measures are essential to prevent unauthorised access and maintain the integrity of industrial systems. Secure remote access in OT and ICS environments should provide zero-trust access, enforce MFA, set access permissions according to the principle of least privilege, and adopt controls like a full audit log.
Regulatory Requirements
Digitisation and modernisation force the industrial environment to reevaluate its cybersecurity posture. Critical infrastructure systems in essential operations must ensure high reliability and comply with rigorous standards. Industrial organisations are recommended to plan and implement unified security protection across their critical infrastructure.
Between all these phenomena, the ongoing automation of manufacturing and industrial practices, incorporating IoT, cloud, AI, and cyber-physical systems into production, modernising and harmonising legacy systems, and complying with cybersecurity regulations, industrial organisations are faced with creating secure OT— and ICS-centric solutions.
Key Principles for Building Resilient Remote Access
In the dynamic world of industrial automation, remote access should facilitate encrypted end-to-end communication, allowing engineers, technicians, and operators to monitor, diagnose, and manage OT and industrial control systems (ICS) with ease while providing full control for asset owners.
The solution lies in striking a balance: How can we maintain the reliability of legacy systems while utilising the agility and insights offered by modern technology? ABB Ability™ Secure Remote Access (ABB Ability™ SRA) is a solution crafted for OT and ICS environments. The aim is to deliver streamlined, secure, remote access that enables businesses to adopt innovative solutions while safeguarding the core components of their infrastructure. It is intended to maximise the potential of operational data without sacrificing stability.
Outbound Connection Only
Legacy systems carry more risk than modern counterparts because of their obsolete technology and lack of current security measures. Connecting them directly to the internet increases their vulnerabilities, so it’s crucial to keep them isolated from the network with no open inbound ports. Implementing multiple layers of secured networks between operational technology (OT) and the internet is advisable; remote access software should function without needing any inbound firewall openings.
Secure and Authenticated Connection
The primary objective of remote access in industrial organisations operating across diverse environments and products is to establish secure connections for both internal staff and external partners. This involves assessing and mitigating security and operational risks for each connected asset while creating a detailed network map that outlines asset zones and communication flows. A recommended solution is a secure communication protocol within remote access software that leverages mutual Transport Layer Security (mTLS) with digital certificates to ensure the secure transmission of sensitive data.
Identity and Access Management
A significant gap in many industrial setups is the absence of robust authentication and auditing mechanisms, especially for remote and third-party access. Credential mismanagement is one well-exhibited challenge to manage with the vast array of vendor-specific applications and devices requiring multiple levels of access privileges that operate on the OT network. Adopting industrial identity and access management eliminates the hassle, it provides identity authentication that verifies the identity of users attempting to gain access to critical systems - role-based access control that assigns access permissions and privileges based on user roles and responsibilities; and credential management that manages users’ digital identities and credentials to ensure validity and prevent unauthorized access. Both the endpoint user and target system must authenticate each other, preferably through single sign-on (SSO). ABB Ability™ SRA can provide authentication and access control services for legacy systems without built-in verification capabilities.
User Experience
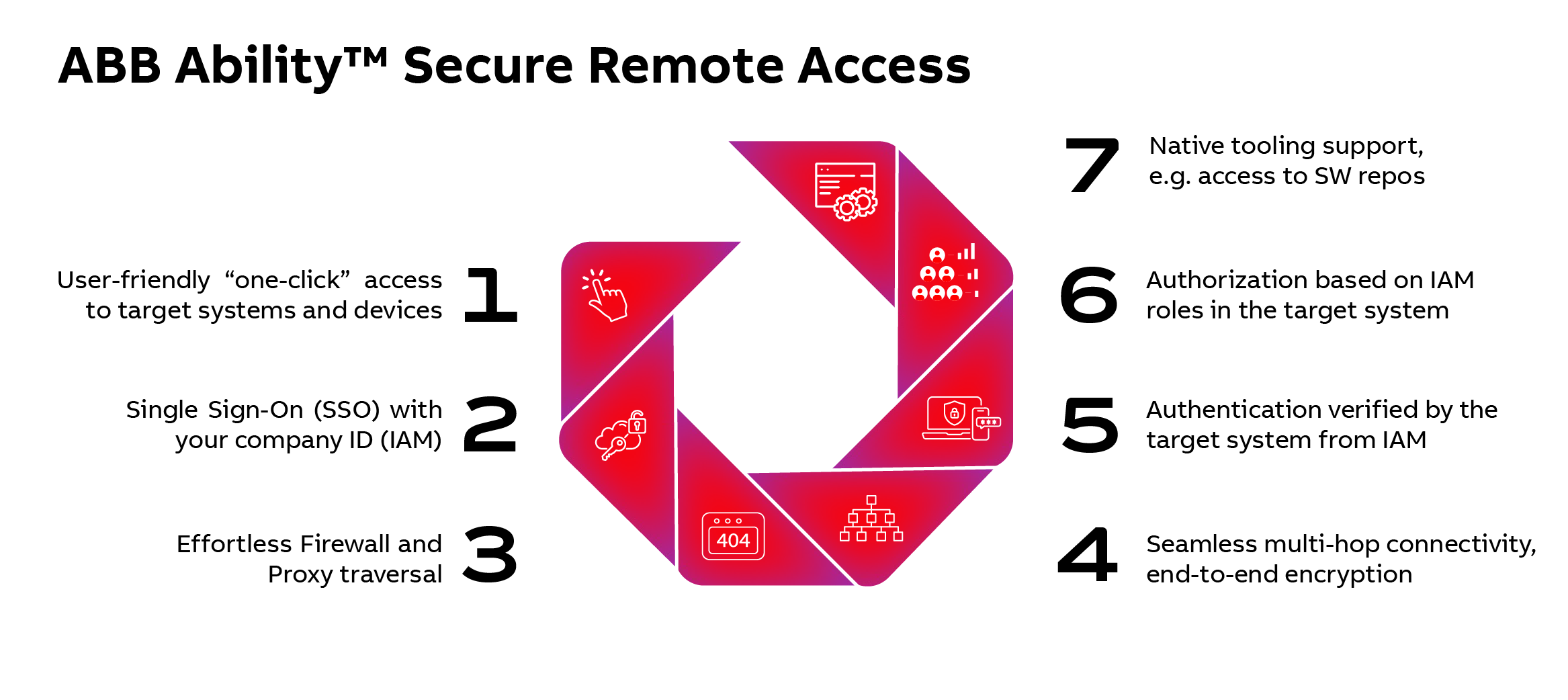
A well-designed interface boosts productivity by helping users complete tasks more efficiently. ABB Ability™ SRA offers an intuitive user experience, allowing users to select resources on the target OT device or ICS, after which the process runs automatically. Single Sign-On (SSO) and access rights verification take place seamlessly in the background, requiring no user input and ensuring the selected resource is opened promptly.
Using native tools for maintenance operations improves productivity and user experience.
Software Updates
Among the best OT and ICS security practices, network segmentation is regarded as the most effective in ensuring security by isolating systems from the internet and other networks. However, this also limits direct access to routine software updates. To overcome this, remote access software can securely connect OT devices and ICS software to repositories to enable regular updates with minimal risk.
Control and Audit
Asset owners must have complete access to remote access audit logs and the control dashboard, allowing them to enable/disable remote access or set a schedule for its availability. OT devices and ICS should maintain audit logs to track user actions and report them to a central SIEM (Security Information and Event Monitoring) system. Remote access software should record events related to user connections to resources.
ABB Ability™ SRA is The Solution for OT Remote Access Services
At its core, ABB Ability™ SRA is a component built to create a secure connection to remote devices. Essentially, it solves the problem of "How do you reach and control remote devices behind a firewall and/or without direct internet connection?". The key idea is to be secure and easy to use.
Patented, secure, and simple to install, with no changes to existing networks
See the SERVICE section for the setup and configuration of VtrinSRA
Enable Remote Access with ABB Ability™ SRA
Simplified Workflow for Engineers
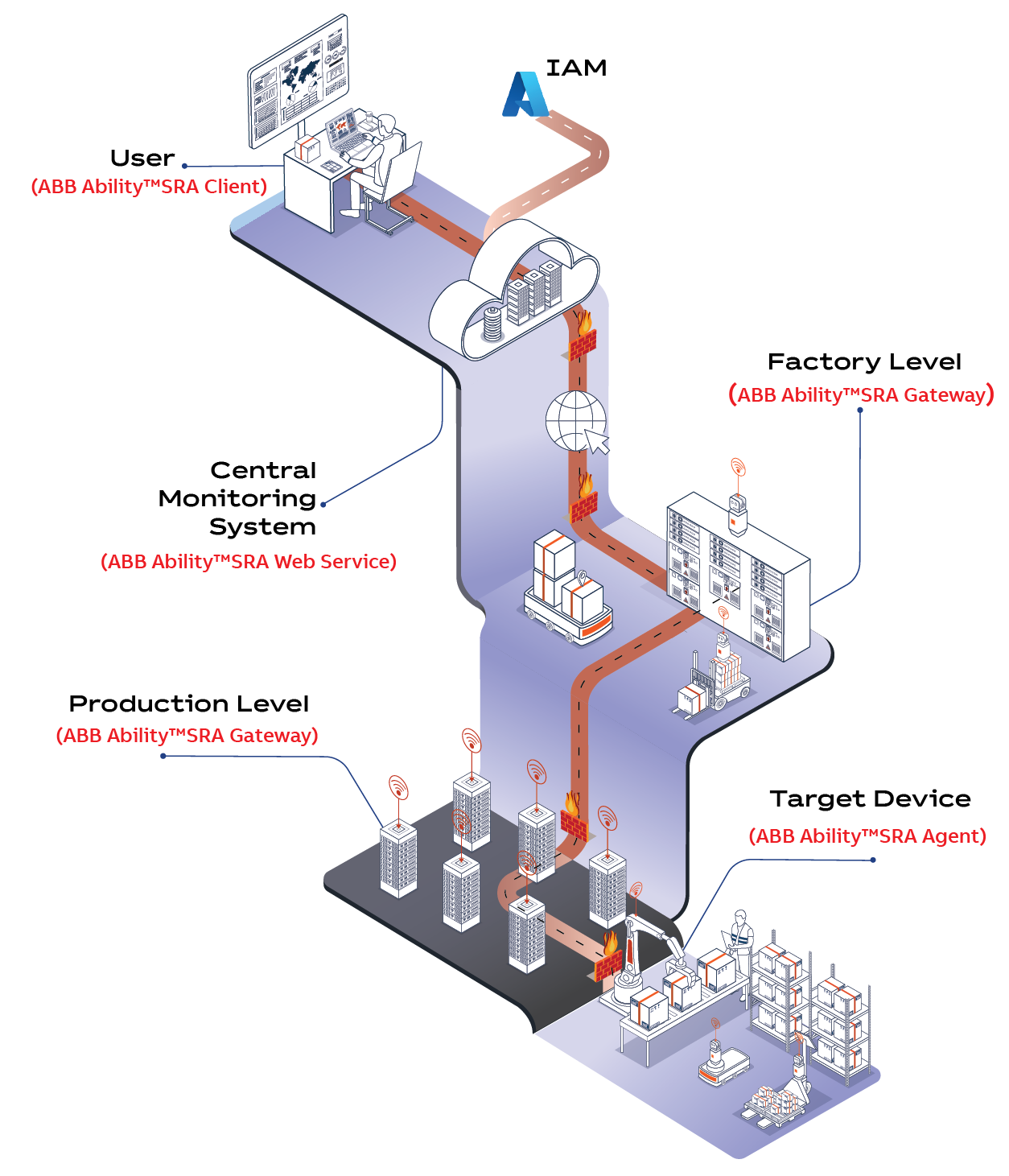
The user can connect to the ABB Ability™ SRA web service using their normal company user account without requiring additional login; ABB Ability™ SRA validates their authentication from the company IAM.
In the ABB Ability™ SRA web service, users can browse the end customer target systems granted to them. The customer systems can be organised in multiple ways according to business needs.
When the user finds the target system requiring remote maintenance, the connection to it can be created by selecting the native tool from the context menu of the target system. The connection is automatically created between the target system and the user's computer, and the selected tool is opened on the user's computer to start the maintenance work.
End-Customer Control of Remote Maintenance and Access
End customers retain full authority over the definition of permitted maintenance activities and access control policies. Target systems equipped with the ABB Ability™ SRA agent autonomously register with the ABB Ability™ SRA web service via a mutually authenticated, secure connection.
Through dedicated control dashboards, end customers can specify the authorised maintenance tools, define required user profiles for access rights management, and enforce access control policies. They can also regulate the timing and conditions under which remote connections are permitted.
Additionally, customers can monitor and review audit logs, configure event-driven notifications, and, if desired, integrate event data automatically into their Security Information and Event Management (SIEM) systems for enhanced security monitoring and compliance.
Target Device: Verify User Authentication
ABB Ability™ SRA enables target device connection to the company's IAM system to verify user authentication and roles when a user connects to it. This process ensures that only authorised personnel can access and perform maintenance on specific customer systems. Furthermore, this integration with the company's IAM automates the management of user access right to the process for revoking user access when they leave the company or a new service engineer joins, allowing the user with the right permit within the company's IAM to automatically enables access to the relevant target systems through ABB Ability™ SRA, streamlining the onboarding process. This eliminates the need for manual updates and ensures consistent and up-to-date access control.
In case the target device is not capable of an IAM connection to verify user authentication, the ABB Ability™ SRA agent can handle the task and also the role-based access control. This enables security implementation for legacy devices.
End-to-end Secure Connection
An ABB Ability™ SRA connection from the ABB Ability™ SRA web service to the target system can contain multiple intermediate ABB Ability™ SRA agents that have certificate-based, mutually authenticated, secure connections. All connections from the user to the target system and from the target system to IAM, and so on, are end-to-end encrypted to protect against man-in-the-middle attacks. Multi-hop connectivity passes through firewalls and proxy servers without requiring additional configurations, making it easy to set up and maintain.
Sales Material
BROCHURES
ABB Ability™ Secure Remote Access Brochures
VIDEO
ABB Ability™ Secure Remote Access teaser video
PRESENTATION
Updated 3 months ago
